[Avg. reading time: 22 minutes]
Faker
Faker: A Python Library for Generating Fake Data
Faker is a powerful Python library that generates realistic fake data for various purposes. It’s particularly useful for:
-
Testing: Populating databases, testing APIs, and stress-testing applications with realistic-looking data.
-
Development: Creating sample data for prototyping and demonstrations.
-
Data Science: Generating synthetic datasets for training and testing machine learning models.
-
Privacy: Anonymizing real data for sharing or testing while preserving data structures and distributions.
Key Features:
-
Wide Range of Data Types: Generates names, addresses, emails, phone numbers, credit card details, dates, companies, jobs, texts, and much more.
-
Customization: Allows you to customize the data generated using various parameters and providers.
-
Locale Support: Supports multiple locales, allowing you to generate data in different languages and regions.
-
Easy to Use: Simple and intuitive API with clear documentation.
from faker import Faker
fake = Faker()
print(fake.name()) # Output: A randomly generated name
print(fake.email()) # Output: A randomly generated email address
print(fake.address()) # Output: A randomly generated address
print(fake.date_of_birth()) # Output: A randomly generated date of birth
Using Faker in Data World
Data Exploration and Analysis: Generate synthetic datasets with controlled characteristics to explore data analysis techniques and algorithms.
Data Visualization: Create sample data to visualize different data distributions and patterns.
Data Cleaning and Transformation: Test data cleaning and transformation pipelines with realistic-looking dirty data.
Data Modeling: Build and test data models using synthetic data before applying them to real-world data.
Using Faker in IoT World
IoT Device Simulation: Simulate sensor data from various IoT devices, such as temperature, humidity, and location data.
IoT System Testing: Test IoT systems and applications with realistic-looking sensor data streams.
IoT Data Analysis: Generate synthetic IoT data for training and testing machine learning models for tasks like anomaly detection and predictive maintenance.
IoT Data Visualization: Create visualizations of simulated IoT data to gain insights into system behavior.
Luhn Algorithm (pronounced as Loon)
Used to detect accidental errors in data entry or transmission, particularly single-digit errors and transposition of adjacent digits.
The Luhn algorithm, also known as the modulus 10 or mod 10 algorithm, is a simple checksum formula used to validate a variety of identification numbers, such as credit card numbers, IMEI numbers and so on.
- Step 1: Starting from the rightmost digit, double the value of every second digit.
- Step 2: If doubling of a number results in a two digit number, then add the digts to get a single digit number.
- Step 3: Now sum all the final digits.
- Step 4: If the sum is divisible by 10 then its a valid number.
Example: 4532015112830366
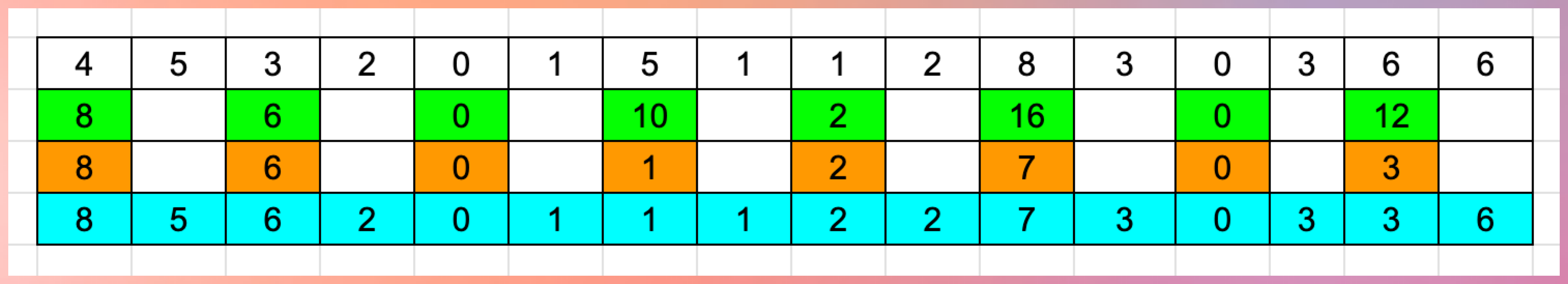
Key Features
- Can detect 100% of single-digit errors
- Can detect around 98% of transposition errors
- Simple mathematical operations (addition and multiplication)
- Low computational overhead
Limitations
- Not cryptographically secure
- Cannot detect all possible errors
- Some error types (like multiple transpositions) might go undetected
Common Use Cases
- Device Authentication: Validating device identifiers
- Asset Tracking: Verifying equipment serial numbers
- Smart Meter Reading Validation: Ensuring meter readings are transmitted correctly
- Sensor Data Integrity: Basic error detection in sensor data transmission
git clone https://github.com/gchandra10/python_faker_demo.git
Damm Algorithm
The Damm Algorithm is a check digit algorithm created by H. Michael Damm in 2004. It uses a checksum technique intended to identify mistakes in data entry or transmission, especially when it comes to number sequences.
Perfect Error Detection:
- Detects all single-digit errors
- Detects all adjacent transposition errors
- No false positives or false negatives
To check where 234 is valid number
Start: interim = 0
First digit (2):
- Row = 0 (current interim)
- Column = 2 (current digit)
- table[0][2] = 1
- New interim = 1
Second digit (3):
- Row = 1 (current interim)
- Column = 3 (current digit)
- table[1][3] = 2
- New interim = 2
Third digit (4):
- Row = 2 (current interim)
- Column = 4 (current digit)
- table[2][4] = 8
- Final interim = 8 (this becomes check digit)
As the final interim is not Zero this is not a valid number as per Damm Algorithm.
[0, 3, 1, 7, 5, 9, 8, 6, 4, 2],
[7, 0, 9, 2, 1, 5, 4, 8, 6, 3],
[4, 2, 0, 6, 8, 7, 1, 3, 5, 9],
[1, 7, 5, 0, 9, 8, 3, 4, 2, 6],
[6, 1, 2, 3, 0, 4, 5, 9, 7, 8],
[3, 6, 7, 4, 2, 0, 9, 5, 8, 1],
[5, 8, 6, 9, 7, 2, 0, 1, 3, 4],
[8, 9, 4, 5, 3, 6, 2, 0, 1, 7],
[9, 4, 3, 8, 6, 1, 7, 2, 0, 5],
[2, 5, 8, 1, 4, 3, 6, 7, 9, 0]
Lets try 57240 and someone entered 57340.
Luhn is like a spell checker and Damm is Grammar checker.
IOT Uses Cases with Algorithms
| Use Case | Algorithm Used | Description |
|---|---|---|
| Smart Metering (Electricity, Water, Gas) | Luhn | Consumer account numbers and meter IDs can use the Luhn algorithm to validate input during billing and monitoring. |
| IoT-based Credit Card Transactions | Luhn | When smart vending machines or POS terminals process card payments, Luhn ensures credit card numbers are valid. |
| IMEI Validation in Smart Devices | Luhn | IoT-enabled mobile and tracking devices use Luhn to validate IMEI numbers for device authentication. |
| Smart Parking Ticketing Systems | Luhn | Parking meters with IoT sensors can validate vehicle plate numbers or digital parking tickets using the Luhn algorithm. |
| Industrial IoT (IIoT) Sensor IDs | Damm | Factory sensors and devices generate unique IDs with the Damm algorithm to prevent ID entry errors and misconfigurations. |
| IoT-based Asset Tracking | Damm | Logistics and supply chain IoT devices use Damm to ensure tracking codes are error-free and resistant to transposition mistakes. |
| Connected Health Devices (Wearables, ECG Monitors) | Damm | Unique patient monitoring device IDs use Damm for error-free identification in hospital IoT systems. |
| IoT-enabled Vehicle Identification | Damm | Vehicle chassis numbers and VINs in IoT-based fleet management use Damm for better error detection. |
| Feature | Luhn Algorithm | Damm Algorithm |
|---|---|---|
| Type | Modulus-10 checksum | Noncommutative quasigroup checksum |
| Use Case | Credit card numbers, IMEI, etc. | Error detection in numeric sequences |
| Mathematical Basis | Weighted sum with modulus 10 | Quasigroup operations |
| Error Detection | Detects single-digit errors and most transpositions | Detects all single-digit and adjacent transposition errors |
| Processing Complexity | Simple addition and modulus operation | More complex due to quasigroup operations |
| Strengths | Simple and widely adopted | Stronger error detection capabilities |
| Weaknesses | Cannot detect all double transpositions | Less widely used and understood |
| Performance | Efficient for real-time validation | Slightly more computationally intensive |
For Firmware updates we can use SHA-256 or SHA-512 (Hashing Algorithms)